Understanding SCIM Provisioning | A Comprehensive Guide on the System for Cross-domain Identity Management for users directory management
by Alexandre Dedourges, DevSec

SSO will enable employees to save a significant amount of time by simplifying the authentication process and avoid manual provisioning. If you want to read more about SSO, you can read what is Single Sign-On. However, in order to guarantee optimal security and identity integrity, it is better to use SCIM with it.
SCIM (System for Cross-domain Identity Management) is an open standard for automating the exchange of user identity information between IT systems. The feature exists in many identity providers like Okta or Microsoft Azure. It is particularly useful when you are using - or considering to use - SSO.
Small reminder about SSO and why you should use SCIM with it
Single Sign-On is a method that allows a user to log in with a single ID to any of several software systems. It allows to connect a user with all the applications they need for their work activity. SSO is particularly handy in the case where a company uses several SaaS as part of its activity. Thanks to SSO, identity management is therefore simplified. However, it remains necessary to manage changes that occur on these identities in order to guarantee the integrity and security of our system. That’s what the SCIM will enable, by simplifying the update of identity data.
SCIM provisioning automates the update of identities
As a company grows and expands, the number of employees increases accordingly. Therefore, the number of identities to be handled becomes bigger and bigger, and the work of IT teams gets more and more complex to sync data between systems. When a new employee arrives or when someone changes their name, this means identities need to be handled, created or updated. Making these changes by hand would be a long and tedious job for your IT teams - especially in the context of rapid growth for your company. That’s where SCIM comes in. SCIM is a protocol created in 2011, to anticipate the influx of SSOs. It allows you to stop worrying about user provisioning As a matter of fact, once you set it up with your SSO, each identity change on the identity provider’s side will be taken into account and spread out on all the services that use this SSO. Thus the security of your system will be preserved.
Provisioning use cases
For instance, an employee who left your company will no longer be able to access the services they used. Similarly, someone who changed their name after getting married will have their profile updated on all their services. To sum up, SCIM enables you to keep data up-to-date to avoid any problems. Indeed, according to a study conducted by Beyond Identity, 83% of employees have already kept user account to their former companies after leaving them. What’s more, 56% of them have tried to harm their former employers by using their previous login information. Lastly, 74% of employers claim to have been negatively impacted by an employee who has kept their access info. That’s why keeping identity information up-to-date is crucial for companies. This is known as identity lifecycle management, with Cryptr you can implement this lifecycle through SCIM with ease for your Organizations.
Benefits of SCIM provisioning : a standard for provisioning integration
As the use of SSO increases, the SCIM standard is becoming more and more popular in the enterprise world. Indeed, it is used by a great number of companies that have set up SSOs. That’s one of the reasons why it’s so solid. With SCIM, user identity data can be communicated everywhere in the same way, which makes its use much easier. Data is transferred in the same manner between various services and applications. Thanks to this standardization of data, you can automate provisioning process and lifecycles can be automated. It allows for the management of roles, groups and permissions in a single location. With data being transmitted automatically, the teams no longer need to change all information on every single platform.
User and group through schemas and extension models
SCIM is primarily based on a common user schema, a group schema and extension models. The latter are exchanged via an HTTP protocol which we’ll expand on in the next section. A SCIM request uses also built on an object model where a resource is the common denominator and all SCIM objects are derived from it. For it to be considered as a resource, it must have the id, externalId and meta attributes. These 3 attributes form for the basis of a resource. Other elements will expand this resource, such as a User, an EnterpriseUser, a Group…
How SCIM work: a standard that uses API REST
SCIM operating model is based on JSON (JavaScript Object Notation) and REST (REpresentational State Transfer). The use of the SCIM API will allow for user update through CRUD (Create, Read Update, Delete) for all of the concerned systems and applications. In order to create, update or delete a user, it will be necessary to use API requests. SCIM provides an easy way to handle user accounts through a SCIM endpoint, making it easier for IT teams. Without SCIM, it is more complicated to automate user provisioning, leading to potential inconsistencies and manual errors.
SCIM implementation: the SCIM Endpoints
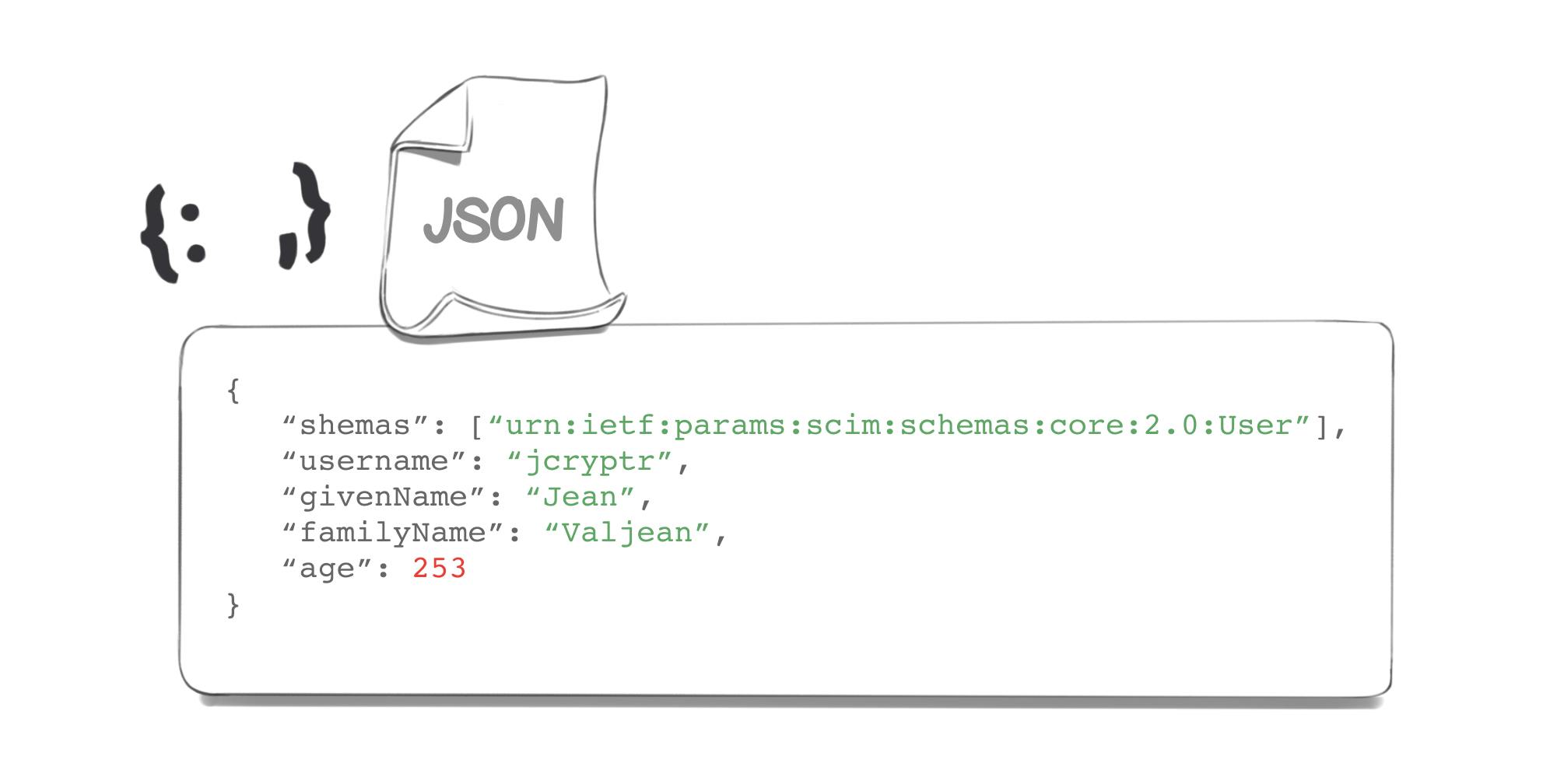
Let’s say a new employee joins Cryptr. Thus, a “User” object will have to be created. This object will be made of different attributes, such as “Name”, “First name”, “Age”... Besides, the info will have to be spread out to all the SaaS tools and applications so that the new employee will be able to access all the tools necessary to their work.
This will be the JSON structure we could have to be transmitting:
In order to handle these structures, a list of basic Endpoints is available directly through the SCIM protocol:

We will now have to use requests in order to transmit data to all our applications. To do so, various HTTP methods exist:
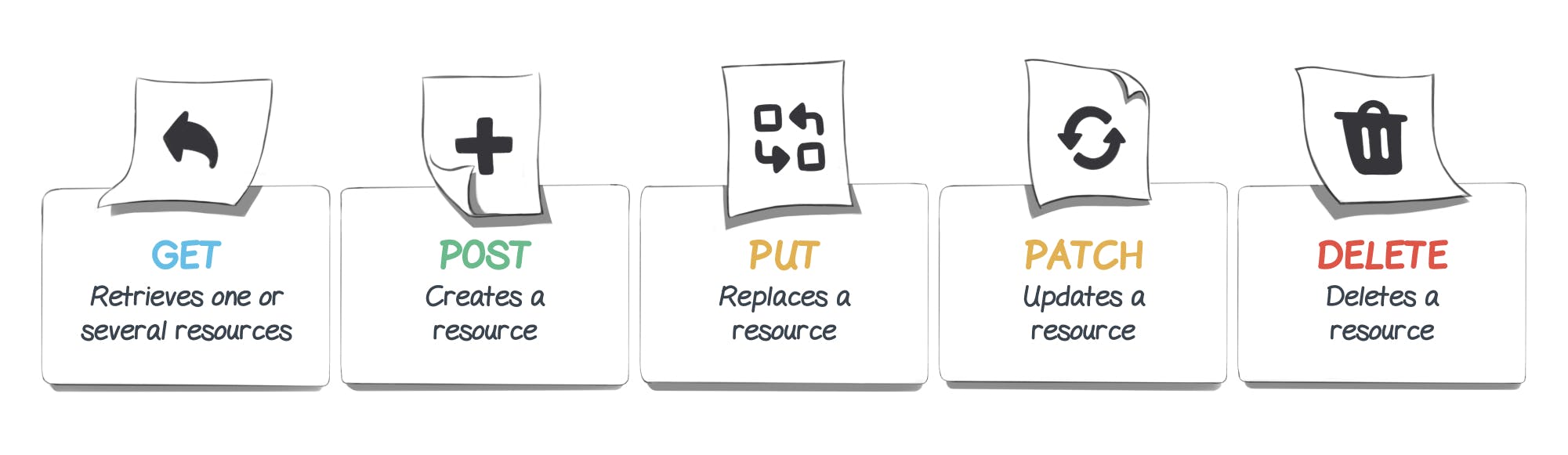
Thus we’ll use a POST method, since - as shown by the table above - the POST method allows for resource creation, as opposed to the other methods.
User creation via HTTP POST request appears under the following format:

Which, with the aforementioned example, would yield:

Here, we work with version #2 of the SCIM API and we want to create a new user - so we’ll work on the “users” resource. Once our POST request is completed, our user will be created on the basis of the parameters provided in the JSON format. If the requests goes through, a JSON response will be sent and can take the following form:
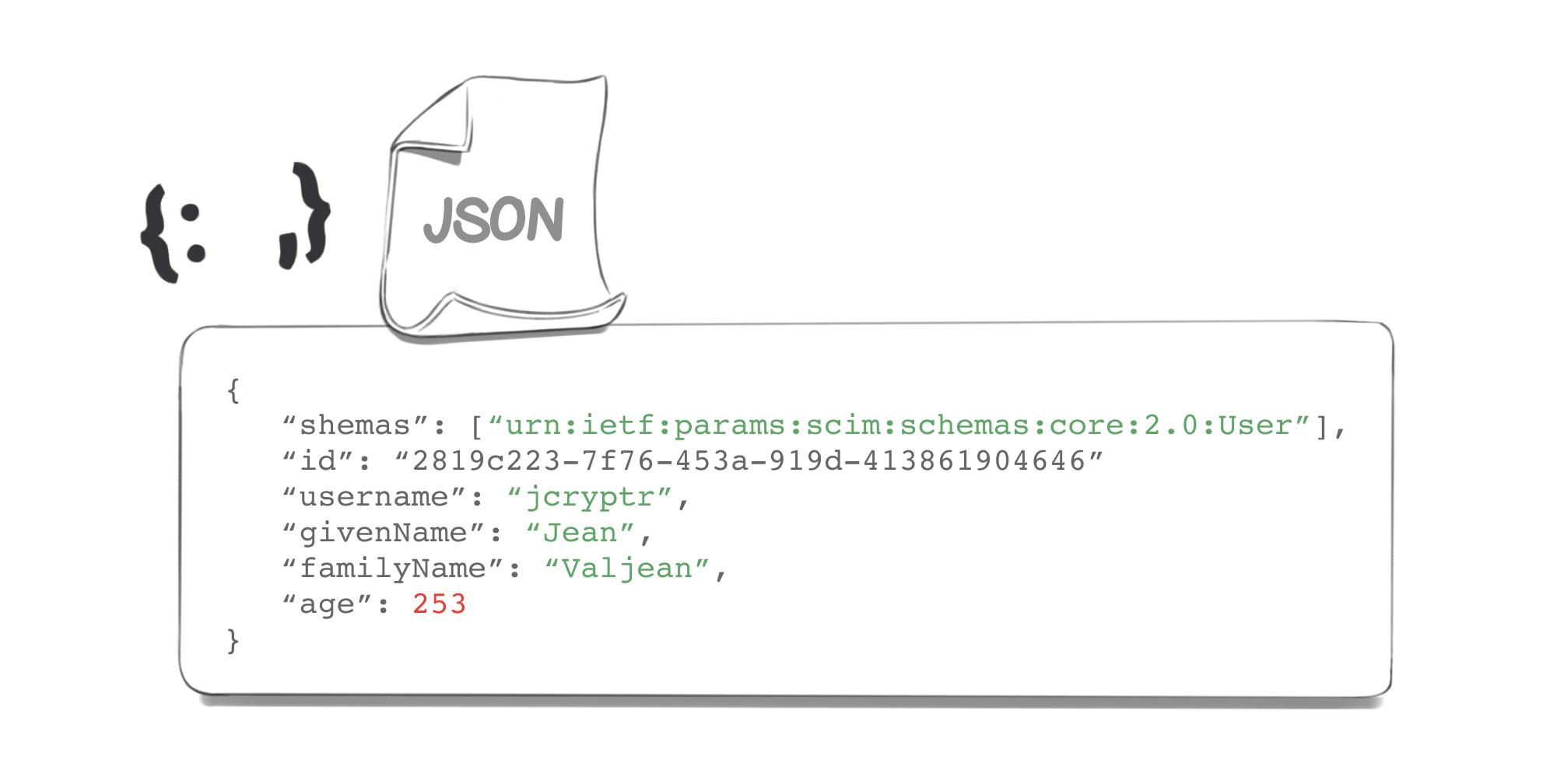
We can see that an ID has been created, which will allow us to identify our user more easily in the future.
For the other methods, the request will be virtually the same - with one exception: the addition of the ID parameter to our URL (of course, we’ll also have to use the correct method):

A classic provisioning use case with Microsoft Entra ID (Azure Active Directory)
Managing user access efficiently is crucial for any organization and many of them use Microsoft to manage user data. Microsoft Entra ID (formerly Azure Active Directory) offers a solution for user provisioning and deprovisioning. With Microsoft, you can effectively manage user lifecycle events, ensuring that user provisioning and deprovisioning are seamless and secure. Ultimately, SCIM solves the challenges of user management, allowing businesses to focus on what matters most. However, implementing a solution in your system that accepts SCIM can take time. This is why Cryptr was thought of. So that you can focus on your own needs.
Adopt SCIM: a tool combining security, productivity and user experience
In a nutshell, the SCIM protocol allows for better identity management. By combining security, productivity and user experience, it has become a “must-have” for any company using an SSO. Besides, a service provider’s ability to be “SSO-friendly” is becoming more and more important, and even a necessity. Therefore, one of the objectives for SaaS app is to become “SSO ready”, i.e. to be able to connect to the various types of SSO and identity and access management solutions that they may encounter through their clients or prospects. Consequently, meeting this requirement is both a matter of security and business when it comes to growing your market and contracting with clients who have such expectations. With just a few lines of code, Cryptr can make your authentication compatible with all types of SSOs (SAML, ADFS, OIDC) and identity providers (Okta, Ping Identity, Auth0, OneLogin, Google,...) that you might encounter. Of course, the SCIM protocol which we’ve just addressed in this article will also be covered! It will allow you to adopt SSOs with ease.
Implement SCIM with Cryptr : a provisioning service layer
Integrating SCIM with Cryptr offers ease in your management of user life cycles. In fact, Cryptr will connect between you and the different IdPs of your customers. The SCIM Server sends us the data that we receive by playing the role of SCIM client. Once we have received the data, we can store the users for you or simply send you the provisioning information in a standardized manner. Additionally, Cryptr leverages an event-driven system using webhooks, which makes it easy to integrate, highly secure, and developer-friendly, allowing you to react to events in real-time and manage user data efficiently. Best of all, no prior knowledge of SCIM is required, Cryptr simplifies the adoption process, making it easy for your teams to implement without needing to dive into the SCIM protocol specifics.
With Cryptr, developers can use SCIM and also seamlessly connect their customers to any SSO provider. These two solutions, SCIM provisioning with Cryptr Directory Sync and SSO integration are independent but complement each other perfectly. You can choose to adopt one or both depending on your needs, ensuring a smooth, secure, and flexible user management experience.
Moreover, Cryptr provides a dedicated feature to assist your client's IT administrator in setting up SCIM auto-provisioning in under 5 minutes. He set up provisioning through a beautifully designed and intuitive interface, administrators are guided step-by-step, making the entire configuration process straightforward and efficient.
Add enterprise SSO for free
Cryptr simplifies user management for your business: quick setup, guaranteed security, and multiple free features. With robust authentication and easy, fast configuration, we meet businesses' security needs hassle-free.